Black Box Testing, also known as functional testing, is the process of exercising an application at a user level without having knowledge of its internal design or structures. The objective is to identify bugs or other non-conformance with the requirements.
What is black box testing?
Black Box Testing is a software testing method where the software’s internal structure, design, and system implementation details are unknown to the tester. In the black box software testing approach, the tester mainly focuses on the inputs and outputs of the software under test without any prior knowledge of the internal code.
Black Box Testing aims to verify that the software functions according to its specified requirements. In this process, testers derive test cases based on the system’s specifications and use these test cases to evaluate the correctness of the outputs in response to various inputs. This method helps in finding the system’s behavior, functionality, and user interactions without knowing the internal code.
For example, if you want to test the login page then you don’t need to know whether it’s coding ASP.net or PHP.
Types Of BlackBox Testing
There are several major types of black box testing in software engineering including functional testing, non-functional testing, and regression testing.
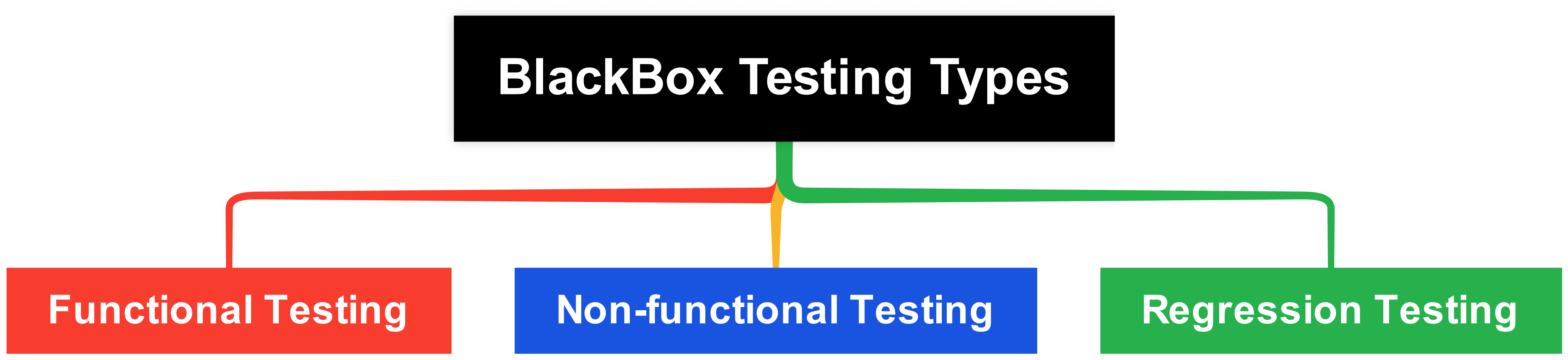
Functional Testing
Functional testing evaluates specific functions and features of the software system. It verifies correct behavior for elements like the user interface, database, APIs, and security mechanisms. For example, functional tests would validate that money is successfully transferred when the correct PIN is entered and that the transaction fails with an incorrect PIN.
Examples of functional testing techniques include:
Non-functional Testing
Non-functional testing analyzes quality attributes and performance characteristics of the system instead of functional behaviors. Non-functional tests evaluate metrics like reliability, compatibility, usability, security, and ability to handle maximum load.
Examples of Non-functional testing techniques include:
Regression Testing
Regression Testing ensures new software doesn’t adversely affect existing ones. It involves retesting executed test cases to spot irregularities, ensuring new code doesn’t impact existing functionality.
Tools Used for Black Box Testing:
Tools for regression testing include:
Black box testing advantages
- Easier to understand and maintain
- Easy to use techniques which could be learned easily
- More software independent
Black box testing has following disadvantages
- Cannot give 100% test coverage so manual testing could not ensure perfect quality.
- It takess more time to complete. As it needs users expertise and most of manual tests are done by users.
Black Box Testing Techniques
There are many black-box testing techniques. We will discuss some important here.
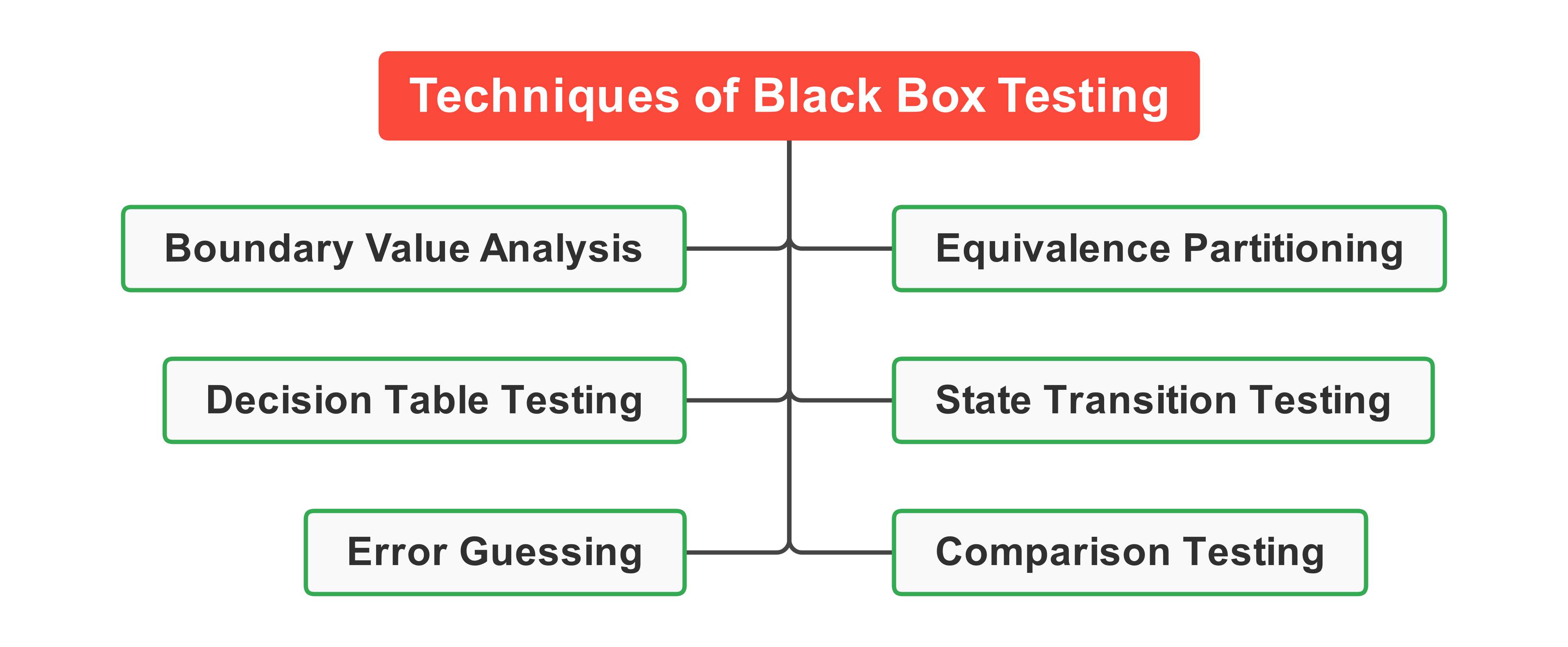
Equivalence Partitioning (EP)
Equivalence partitioning divides inputs into classes that are expected to exhibit similar behavior, allowing testers to treat each partition equivalently. This technique categorizes inputs as either valid or invalid. Valid partitions contain values accepted by the system under test. Invalid partitions contain values rejected by the system.
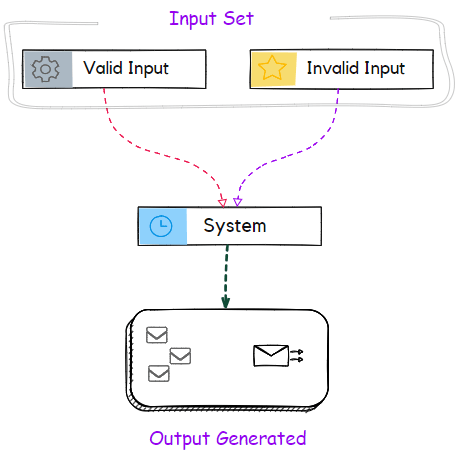
When applying equivalence partitioning, remember:
- Each input value belongs to exactly one partition
- Both valid and invalid partitions must be tested
- Invalid values should be tested separately to avoid masking issues
- Partitions can be further subdivided if additional granularity is needed
To achieve full coverage, testers must select at least one representative value from every defined partition. Testing two values from the same partition does not increase coverage. Overall, this method allows testers to efficiently sample inputs without having to exhaustively test every possible value. By methodically testing valid and invalid classes of data, confidence grows that the system handles categories of inputs correctly.
Equivalence Partitioning (EP) Example
Consider a software application that validates phone numbers. The application only accepts 10-digit numbers – shorter or longer numbers are invalid. We can apply equivalence partitioning to this validation logic. The input domain is phone numbers, which we can divide into two partitions:
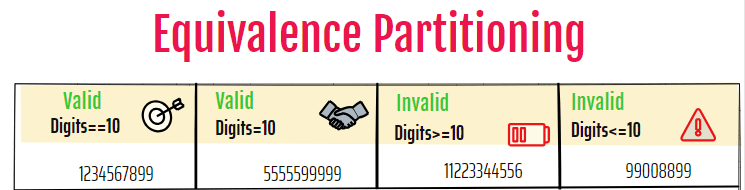
- Valid partition: Consists of 10-digit numbers. These values should be accepted by the application.
- Invalid partition: Consists of numbers less than or greater than 10 digits. These values should be rejected by the application and produce an error message.
When a user enters a phone number, the application checks which partition it falls into:
If the number contains exactly 10 digits, it falls into the valid partition. The application accepts it successfully. If the number contains less than or more than 10 digits, it falls into the invalid partition. The application rejects it and shows an error to the user.
So by methodically testing inputs from the valid and invalid partitions, we can verify that the validation logic works as expected using equivalence partitioning.
Boundary Value Analysis
Boundary value analysis, an extension of equivalence partitioning, focuses on testing the limits of valid and invalid partitions. These limits, considered as breaking points with a higher probability of errors, are integral to this technique. Boundary value analysis and equivalence partitioning can be used together as complementary black box testing techniques.
Boundary value analysis tests input values near the edges of valid partitions, where errors are more likely. Partitions have maximum and minimum in-range values. These upper and lower values define the partition boundaries that boundary value analysis targets for testing.
Note:
- A boundary value for a valid partition is a valid boundary value.
- A boundary value for an invalid partition is an invalid boundary value.
- For each variable we check-
- Minimum value.
- Just above the minimum.
- Nominal Value.
- Just below Max value.
- Max value.
Example:
Lets take an example where to apply a job the candidates age should be in between 18 and 32.
| Invalid (min-1) | Valid (min, min + 1, nominal, max – 1, max) | Invalid (max + 1) |
|---|---|---|
| 17 | 18, 19, 24, 31, 32 | 33 |
Decision Table Testing
The decision table testing technique visually maps out different combinations of inputs and outputs, with a focus on validating business rules. It is applicable when a system or component can produce different outputs given various mixes of input conditions.
Decision table testing method identifies the relevant conditions and resulting actions of the test object, presenting them in a table format. Typically, the conditions (often inputs) are shown in the top rows and the actions (usually outputs) are defined in the bottom rows.
The first column provides explanations of the conditions and actions. Each additional column represents one decision rule. The table denotes TRUE conditions and actions with Y, T or 1, FALSE ones with N, F or 0, and irrelevant ones with – or N/A.
The decision table can always be simplified by removing columns for conditions that do not influence the output or have impossible combinations. To achieve 100% coverage, each rules column must be tested at least once. Overall, the tabular format systematically connects inputs to expected results.
| Conditions | Rule – 1 | Rule – 2 | Rule – 3 | Rule – 4 |
|---|---|---|---|---|
| UserName | F | T | F | T |
| Password | F | F | T | T |
| Output | Error Message | Error Message | Error Message | Home Screen |
If you notice the above tabular format then we yhave four cases
- Case1: Both the Username and password is wrong so we are getting Error Message.
- Case2: Username is correct and password is wrong so we will get Error message.
- Case3: Username is wrong and password is correct, we will get Error message.
- Case4: Both the Username and password is correct so we are redirect to Home Screen.
State Transition Testing
State transition testing is a black box technique for systems that behave differently based on current conditions and prior events. The system’s preceding activities are its “state”, while an “event” is an occurrence that triggers transitions between states. State transition diagrams and tables model the states and events causing state changes. A single event can spur different transitions to the same state.
State transition testing Diagram
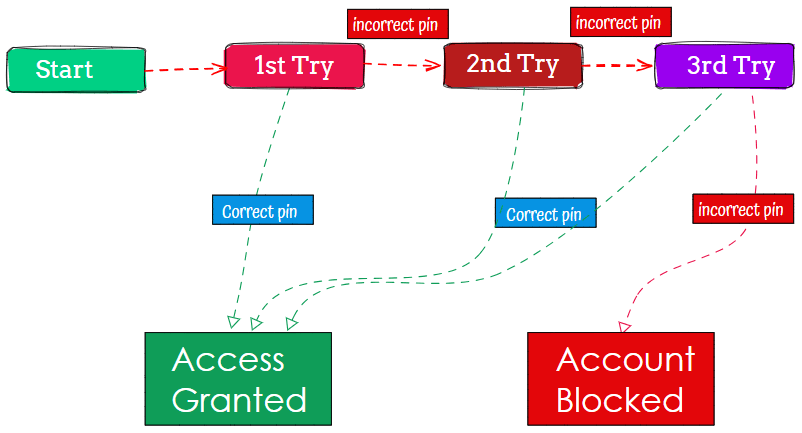
For example, entering a PIN into an ATM is an event. This alters the state, prompting an action like the ATM displaying available services or an error message, depending on whether the PIN is correct.
We can design test cases to check if the system properly executes valid transitions and blocks invalid ones. State transition testing applies to screen-based embedded systems like ATMs, or any transitional software.
We achieve 100% coverage by testing every transition and state at least once. Tracking coverage is aided by the transition diagram or table. Testing all transitions takes priority over testing all states.
Error Guessing
It is a black-box testing technique. It helps us to identify specific errors that might occur in a system by using known or possible error conditions as our test cases. To implement this type of testing, we must first identify the errors or defects that could occur in particular software. Next, our test cases will include inputs designed to produce these known conditions and will check for expected results of failures.
Error guessing is useful during early phases of testing where there may not be enough information available about how a system works. It can also be used when designing test cases for new functionality.
The basic steps to follow when implementing this testing technique are:
- Identify possible conditions that could result in an error, e.g., divide by zero, access invalid memory location. These errors can be identified by requirements specifications or from known problems in related systems, etc.
- Develop a test case for each error conditions identified. It is best to have at least two test cases per condition to cover different possible data sets.
- Execute your test cases and review the results to determine if any errors were found. If an error was found, you can add more test cases or modify existing test cases.
How to do BlackBox Testing?
To perform Black box testing, you should follow these steps:
- Identify the purpose of a class from the requirements document. Based on the requirements document and your experience, what is this class suppose to do?
- Identify how a user will interact with this class from the requirements document and your own experience with the system. How will a user work with this class?
- Identify what data is returned by this class. What type of data is the class returning?
- Identify how to test each method or function in this class. How can you test this method or function?
- Identify the boundary value for each method or function in this class. What are the inputs and outputs for this method or function?
- Determine specific testing approaches, techniques for each requirement, and test case design techniques. How is the testing going to be done?
Conclusion:
Black box testing is an integral part of the software testing process, focused on validating functional requirements without access to internal code and structures. As covered in this article, there are several helpful black box techniques including equivalence partitioning, boundary value analysis, decision table testing, and state transition testing.
When used strategically and in combination, these methods can effectively test a system’s inputs, outputs and functionality from an end-user perspective. To continue mastering test design concepts, I encourage readers to apply these black box testing techniques to sample applications, observe the defect detection rates, and expand their overall quality assurance skills.
Please share any comments or suggestions on how to improve this overview by reaching out in the responses below. Feedback is greatly appreciated as we aim to continuously evolve our testing resources for the community.
